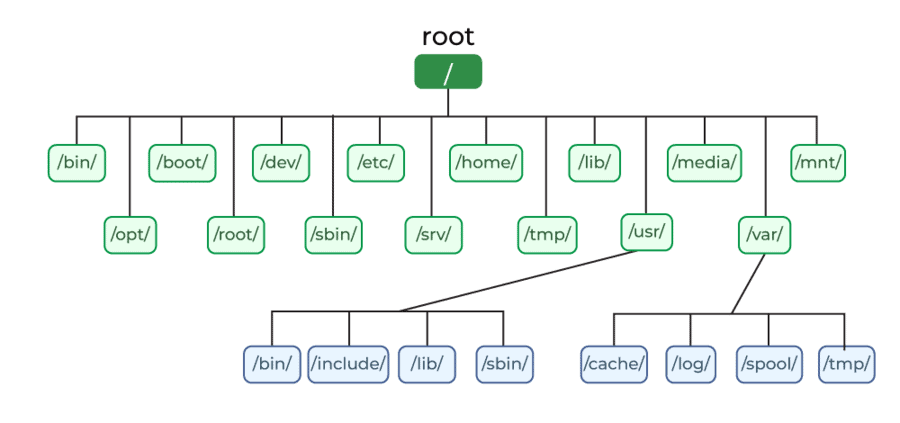
The Unix File System Hierarchy is a foundational structure that organizes files and directories in the Unix operating system.
Understanding it is essential for effective navigation and utilization of the system.
Key Takeaways
- The root directory, ‘/’, is the topmost directory in the Unix file system hierarchy.
- Mount points are established within the root directory to represent separate file systems.
- Symbolic links and hard links are important concepts related to the root directory.
- Device files are located in the /dev directory of the Unix file system hierarchy.
Root Directory
The root directory, also known as ‘/’, is the topmost directory in the Unix file system hierarchy. It serves as the starting point for all other directories and files. Understanding the root directory is crucial to navigating the entire file system effectively.
Within the root directory, different mount points are established to represent separate file systems. These mount points allow various storage devices or partitions to be accessed as separate entities within the file system hierarchy. By mounting different devices or partitions at specific mount points, the Unix file system can efficiently manage and organize data.
Symbolic links and hard links are two important concepts related to the root directory. Symbolic links are shortcuts or references to files or directories located elsewhere in the file system. They provide a way to access a file or directory from a different location without duplicating the original content.
On the other hand, hard links are additional references to the same file or directory. They provide multiple entry points to access the same data, saving storage space.
Binaries and Executables
To understand the functionality of the root directory in the Unix file system hierarchy, it’s essential to delve into the world of binaries and executables. Binaries and executables are the heart of any operating system, including Unix. They’re the files that contain the instructions for the computer to execute specific tasks.
Here are three important aspects to consider when it comes to binaries and executables:
- Shell scripting: Unix provides a powerful shell scripting environment that allows users to automate tasks and create complex scripts. Shell scripts are executable files that contain a series of commands to be executed by the shell. They’re a fundamental tool for system administrators and power users.
- Dynamic linking: Unix systems use dynamic linking to optimize memory usage and improve the efficiency of executables. Dynamic linking allows multiple programs to share the same libraries, reducing redundancy and conserving system resources. It also enables the system to update libraries without recompiling all the executables that depend on them.
- Execution permissions: Unix file permissions play a crucial role in controlling who can execute a binary or executable. The permission bits, such as read, write, and execute, determine whether a file is executable and who can run it. Properly managing execution permissions is essential for security and ensuring that only authorized users can execute sensitive programs.
Understanding the world of binaries and executables is fundamental to navigating the Unix file system hierarchy and harnessing the full potential of the operating system. It allows for innovative approaches to automation, efficient memory management, and robust security measures.
User Home Directories
Now let’s talk about user home directories.
These directories play a crucial role in the Unix file system hierarchy, providing users with a dedicated space to store their personal files and data.
Home directories are structured and organized, allowing users to easily navigate and manage their files.
Additionally, they offer permissions and access controls, ensuring that each user has exclusive access to their own directory.
Moreover, home directories can be customized and personalized according to individual preferences, making them a versatile and user-friendly feature of the Unix file system.
Structure and Organization
User home directories play a crucial role in the structure and organization of the Unix file system hierarchy. They provide users with a designated space to store their personal files and configurations, ensuring that their data remains separate and secure.
Here are three key aspects of user home directories that contribute to the overall organization of the file system:
- File system security: User home directories are protected by file permissions, allowing users to control who can access their files. This provides an extra layer of security, ensuring that sensitive information remains private.
- File system navigation: Each user’s home directory is located under the /home directory, making it easy to navigate and locate specific user files. This hierarchical structure simplifies file management and enables efficient access to user data.
- Personalization and customization: User home directories can be personalized and customized according to individual preferences. Users can create subdirectories, organize files into folders, and configure settings specific to their needs, fostering a personalized and efficient work environment.
Permissions and Access
The permissions and access of user home directories in the Unix file system hierarchy ensure secure and controlled file management for individual users. File ownership plays a crucial role in determining who can access and modify files within their home directories.
Unix uses both symbolic and numeric permissions to define file access rights. Symbolic permissions use letters (r, w, x) to represent read, write, and execute permissions, while numeric permissions use a three-digit code (e.g., 777) to represent the same. The three digits correspond to the permissions of the owner, group, and others, respectively. This system allows users to easily understand and manage file permissions.
Customization and Personalization
After understanding the permissions and access of user home directories in the Unix file system hierarchy, it’s important to explore the customization and personalization options available within these directories. Personalized settings are essential for creating a computing environment that suits your preferences and enhances your productivity.
Here are three customization options that can help you tailor your user home directory to your needs:
- Customizing the shell: You can personalize your command line interface by setting up aliases, customizing the prompt, and configuring environment variables. This allows you to streamline your workflow and automate repetitive tasks.
- Configuring application settings: Many applications store their configuration files in your user home directory. By modifying these files, you can customize the behavior of the applications to better suit your preferences.
- Creating startup scripts: You can write scripts that run automatically when you log in, allowing you to automate tasks or set up your preferred working environment.
System Configuration Files
System Configuration Files play a crucial role in managing the settings and behavior of a Unix system. These files contain important information that determines how the system functions and interacts with its environment. Two key areas that system configuration files cover are system logs and network configuration.
System logs are essential for monitoring and troubleshooting a Unix system. They provide a detailed record of system activities, errors, and warnings. By analyzing system logs, administrators can identify issues and take appropriate actions to resolve them. These logs are typically stored in the /var/log directory and can be accessed using tools like `tail` or `grep`.
On the other hand, network configuration files define the network settings of a Unix system. They determine how the system connects to the network, including IP addresses, DNS servers, and routing tables. These files are usually located in the /etc/network directory and can be edited using text editors like `vi` or `nano`.
To give you a clearer picture, here is a table showcasing some common system configuration files:
| Configuration File | Purpose | Location |
|---|---|---|
| /etc/syslog.conf | Configures system logging behavior | /etc/syslog.conf |
| /etc/network/interfaces | Defines network interface settings | /etc/network/interfaces |
| /etc/hosts | Maps hostnames to IP addresses | /etc/hosts |
| /etc/resolv.conf | Specifies DNS resolver configuration | /etc/resolv.conf |
Understanding and managing these system configuration files is crucial for effectively customizing and maintaining a Unix system. By leveraging these files, you can optimize system performance, troubleshoot issues, and ensure seamless network connectivity.
Device Files
Now let’s talk about device files.
These files play a crucial role in Unix systems as they allow programs to interact with various hardware devices.
Understanding file permissions and the file system structure is essential when working with device files.
File permissions determine who can access and manipulate the device, while the file system structure ensures that the device files are organized and accessible in a logical manner.
File Permissions
File permissions for device files control access to devices in the Unix file system hierarchy. Understanding and managing these permissions is crucial for ensuring the security and proper functioning of your Unix system.
Here are three key aspects to consider when dealing with file permissions for device files:
- Ownership: Each device file is associated with an owner, typically the user who created it. The owner has certain privileges and can control who can access or modify the device.
- Symbolic Notation: Unix uses symbolic notation to represent file permissions. This notation consists of three sets of characters: user permissions, group permissions, and other permissions. Each set can contain three characters: read (r), write (w), and execute (x).
- Access Control: With file permissions, you can set different levels of access control for different users or groups. This ensures that only authorized individuals or processes can interact with the devices.
File System Structure
To fully understand and manage file permissions for device files, it’s essential to grasp the structure of the Unix file system hierarchy. Device files play a crucial role in the file system structure, allowing access to hardware devices such as printers, disks, and terminals. These files are located in the /dev directory, which is a part of the Unix file system hierarchy.
When it comes to file system security, it’s important to protect device files from unauthorized access. This can be achieved by setting appropriate permissions and ownership for these files. By restricting access to device files, you can prevent potential security breaches or accidental modifications.
Additionally, file system maintenance plays a key role in ensuring the proper functioning of device files. Regularly checking for file system errors, optimizing disk space, and performing backups are important tasks for maintaining the integrity and reliability of device files.
Understanding the structure of the Unix file system hierarchy is crucial for effectively managing file system security and maintenance, especially when it comes to device files. By implementing proper permissions and regularly maintaining the file system, you can ensure the security and stability of your Unix system.
Temporary Files and Directories
Temporary files and directories play a crucial role in the Unix file system hierarchy by providing a space for storing transient data that’s used by various processes and applications. When it comes to managing these temporary files and directories, there are certain best practices that can ensure efficiency and organization.
Here are three key points to consider:
- Importance of temporary files in Unix systems: Temporary files are essential in Unix systems as they allow processes to store and access data temporarily. These files are often created during the execution of programs and are used for tasks like caching, logging, and inter-process communication. Without temporary files, the performance and functionality of Unix systems could be severely impacted.
- Best practices for managing temporary directories in Unix: To effectively manage temporary directories, it’s important to regularly clean them up. This can be done by implementing automated processes that remove files older than a certain time period. Additionally, it’s recommended to use separate temporary directories for different purposes to prevent clutter and potential conflicts. It’s also advisable to set appropriate permissions for temporary directories to ensure security and prevent unauthorized access.
- Optimizing temporary file usage: To optimize the usage of temporary files, it’s essential to avoid creating unnecessary files and to remove them when they’re no longer needed. It’s also recommended to use file compression techniques for large temporary files to save disk space. Regular monitoring and auditing of temporary files can help identify any abnormalities or potential issues.
Frequently Asked Questions
How Can I Access the Root Directory in Unix?
To access the root directory in Unix, you need to have the necessary permissions. Alternatively, you can use the command “cd /” to directly navigate to the root directory.
What Are Some Commonly Used Binaries and Executables in Unix?
You’d think that understanding the Unix file system hierarchy would be a bore, but let me tell you, the commonly used binaries and executables in Unix are an innovative bunch. They work efficiently to serve their purposes.
How Can I Find My User Home Directory in Unix?
To find your user home directory in Unix, use the command “echo ~”. The tilde (~) symbol in Unix file paths represents the user’s home directory, making it easy to navigate and access files.
What Are Some Important System Configuration Files in Unix?
You can modify system configuration files in Unix by using text editors or command-line tools. Be cautious when deleting or modifying important files as it can cause system instability or malfunction.
How Do Device Files Work in Unix and What Are Their Purposes?
Device files in Unix, such as character and block devices, serve important purposes. They allow communication with hardware devices, have specific permissions, are created using mknod, and are used and managed by system administrators.

